This topic going ti discuss about five steps of Hacking taking an instance of a Hacker looking to hack a company’s server and having access to all of the data.
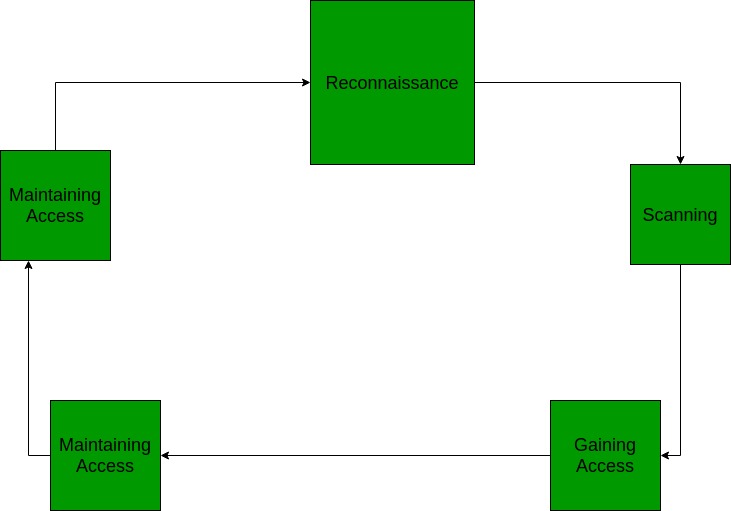
Reconnaissance
This is the primary segment in which the Hacker attempts to gather records approximately the goal. It can also additionally encompass Identifying the Target, locating out the goal’s IP Address Range, Network, DNS records, etc.Let’s expect that an attacker is set to hack a websites’ contacts.
He can also additionally accomplish that by : the use of a seek engine like maltego, getting to know the goal say a internet site (checking links, jobs, activity titles, e-mail, news, etc.), or a device like HTTPTrack to down load the complete internet site for later enumeration, the hacker is capable of decide the following: Staff names, positions, and e-mail addresses.
Scanning
This section consists of utilization of gear like dialers, port scanners, community mappers, sweepers, and vulnerability scanners to experiment data. Hackers are actually in all likelihood searching for any statistics which can assist them perpetrate assault inclusive of laptop names, IP addresses, and person accounts.Now that the hacker has a few fundamental statistics, the hacker now actions to the subsequent section and starts offevolved to check the community for different avenues of attacks. The hacker comes to a decision to apply a pair strategies for this give up to assist map the community (i.E. Kali Linux, Maltego and locate an e-mail to touch to look what e-mail server is being used). The hacker seems for an automatic e-mail if viable or primarily based totally at the statistics amassed he may also determine to e-mail HR with an inquiry approximately a activity posting.
Gaining Access
In this phase, hacker designs the blueprint of the community of the goal with the assist of statistics amassed in the course of Phase 1 and Phase 2. The hacker has completed enumerating and scanning the community and now determine that they have got a a few alternatives to advantage get right of entry to to the community.
For example, say hacker chooses Phishing Attack: The hacker makes a decision to play it secure and use a easy phishing assault to advantage get right of entry to. The hacker makes a decision to infiltrate from the IT department. They see that there were a few current hires and they may be in all likelihood now no longer up to the mark at the strategies yet. A phishing e mail might be despatched the usage of the CTO’s real e mail deal with the usage of a software and despatched out to the techs. The e mail consists of a phishing internet site with a purpose to gather their login and passwords. Using any wide variety of alternatives (tele cell smartphone app, internet site e mail spoofing, Zmail, etc) the hacker sends a e mail asking the customers to login to a brand new Google portal with their credentials. They have already got the Social Engineering Toolkit going for walks and feature despatched an e mail with the server deal with to the customers protecting it with a bitly or tiny url.
Other alternatives consist of growing a opposite TCP/IP shell in a PDF the usage of Metasploit ( can be stuck through junk mail filter). Looking on the occasion calendar they are able to installation a Evil Twin router and attempt to Man withinside the Middle assault customers to advantage get right of entry to. An version of Denial of Service assault, stack primarily based totally buffer overflows, and consultation hijacking might also show to be great.
Maintaining Access
Once a hacker has won get right of entry to, they need to hold that get right of entry to for destiny exploitation and assaults. Once the hacker owns the machine, they are able to use it as a base to release extra assaults.
In this case, the owned machine is every now and then called a zombie machine.Now that the hacker has a couple of e mail debts, the hacker starts to check the debts at the domain. The hacker from this factor creates a brand new administrator account for themselves primarily based totally at the naming shape and try to combo in. As a precaution, the hacker starts to search for and become aware of debts which have now no longer been used for an extended time. The hacker assumes that those debts are possibly both forgotten or now no longer used so that they alternate the password and raise privileges to an administrator as a secondary account if you want to preserve get right of entry to to the network. The hacker may additionally ship out emails to different customers with an exploited document consisting of a PDF with a opposite shell if you want to increase their viable get right of entry to. No overt exploitation or assaults will arise at this time. If there’s no proof of detection, a ready recreation is performed letting the sufferer suppose that not anything changed into disturbed. With get right of entry to to an IT account the hacker starts to make copies of all emails, appointments, contacts, immediate messages, and documents to be looked after via and used later.
Clearing Tracks (so no one can reach them)
Prior to the assault, the attacker might extrade their MAC cope with and run the attacking device via at the least one VPN to assist cowl their identity. They will now no longer supply an immediate assault or any scanning approach that might be deemed “noisy”.
Once get admission to is won and privileges were escalated, the hacker are seeking for to cowl their tracks. This consists of clearing out Sent emails, clearing server logs, temp files, etc. The hacker can even search for indicators of the e-mail company alerting the consumer or feasible unauthorized logins beneathneath their account.
Protect Yourself
- Do now no longer submit records on social media that may be associated with undertaking questions
- Use passwords that can not be damaged with the aid of using brute pressure or guessing.
- Consider 2 issue authentication whilst possible.
- Be cautious of password requests emails. Services like Heroku, Gmail and others will now no longer request to kind in passwords for extra advertising or service.
- Verify supply of contact.
- Before clicking a link, check out it.
- Always experiment a record and by no means click on on batch files.
- Always see the history offerings which can be going for walks to your tool and by no means depend on others’ tool.
- Be certain to have a antivirus mounted and set root passwords for installation.
- Log out of classes and smooth the cache.
Be safe and refrain yourself becoming the target!!
